Understanding the 6 Elements of the Incident Response (IR) Process
By Jared Hrabak, Consulting Cybersecurity Engineer, cStor and MicroAge

From Framework to Building an Incident Response Plan
Thirty years ago if you mentioned “virus” or “worms,” everyone thought you were referring to biology, not the security of your network. However, today it is a very different story. If you have chosen your cybersecurity framework and are on your way to a more mature security posture, it might be time to think about advancing your Incident Response (IR) Plan.
As an Eagle Scout and member of the military, it’s ingrained in me to prepare for any number of potential scenarios. Building contingency plans and conducting rehearsals (a.k.a. “tabletops”) ensures that every member of your team knows what to do when something happens. Anticipating possible scenarios that could impact your business operations and creating action plans are integral to effective incident response.
Defining Incident Response
The Cybersecurity and Infrastructure Security Agency (CISA) defines a cyber incident as “an event occurring on or conducted through a computer network that actually or imminently jeopardizes the confidentiality, integrity or availability of computers, information or communications systems or networks, physical or virtual infrastructure controlled by computers or information systems, or information resident thereon.” CISA considers cyber incident response an important component of information and communications technology (ICT) and of operational technology programs and systems.
Although it’s easy to define a cyber incident, performing incident response effectively is a complex undertaking that requires substantial planning and resources to establish a successful readiness capability. As you create your own incident response plans, make sure you consider all the necessary elements.
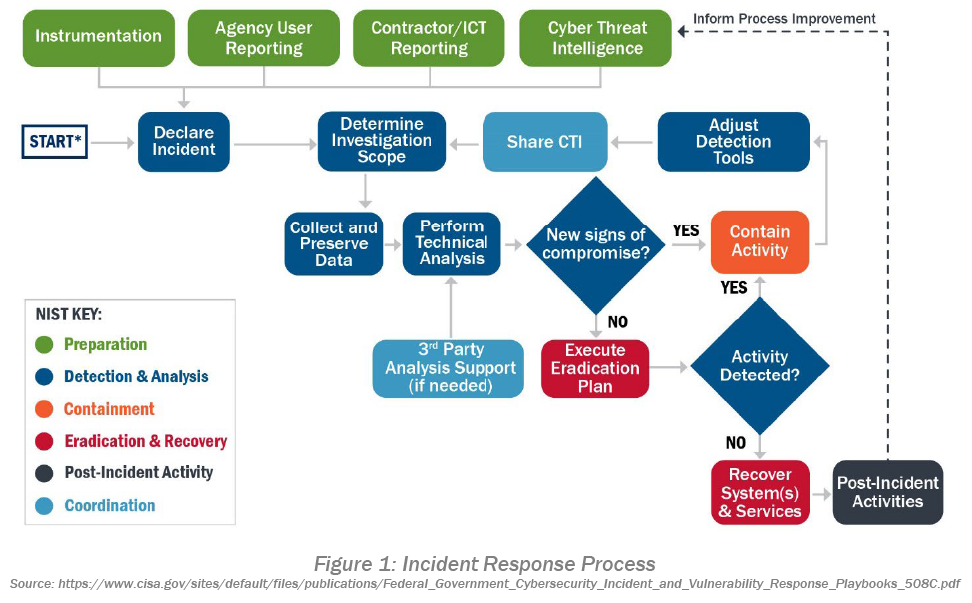
6 Elements of the Incident Response Process
1. Preparation: Start with framing roles and responsibilities to help build contact information, reporting mechanisms and procedures. Asset identification drives the risk level for your organization, which determines the level of response required during the incident. For example, you wouldn’t wake the CEO because you received a phishing email. However, if your corporate shared storage drive was encrypted and was impacting operations, that may warrant an escalation.
This is a great time to create (or dust off) your Business Continuity Plan (BCP). Build relationships with law enforcement and invite them to the table to share key pointers. The Department of Homeland Security (DHS) Critical Infrastructure Cyber Community Voluntary Program (C3) is a program to help get you started. Be sure to define action steps if a breach happens and review your state notification laws to incorporate what will be published, who will be communicating the incident and how often the public should expect regular updates.
2. Detection & Analysis: Different attack vectors will have different detection methods. Depending on your environment, there are various ways to detect incidents ranging from network tools to endpoint protection to a Security Operations Center (SOC). Measure your baseline so you know what normal network traffic, system and user behaviors look like, giving you a clear understanding of everyday operations. This will help the incident handler intelligently identify unusual activity against the baseline. Time is of the essence. It’s critical to stay hot on the trail and use every tool at your disposal to take the appropriate actions as quickly as possible. If you think this sounds overly dramatic, Russian hackers went from a ‘foothold to full-on breach’ in only 19 minutes, and recent estimates say hackers could take only “hours to empty your network.” Time is often not on your side.
3. Containment: Like detection, the strategy for containing an incident will vary. Containing a ransomware attack will require a different approach than mitigating a distributed denial of service (DDoS) attack. Each strategy you develop will need to identify where critical decision-making points exist and the appropriate escalation paths for each. Identifying the time and resources required for containment tactics are vital considerations. It’s important to ensure your internal team and any third-party support resources are all on the same page regarding containment procedures.
4. Eradication and Recovery: Removal of malware or other items from the incident may be necessary to return to normal operations. Containment procedures should provide identification of all systems and users that were affected. This is key information to start the recovery process. Recovery may require tasks such as identifying clean backups, installing patches, rebuilding user profiles and systems, changing passwords and more. Recovery timelines could range from hours to weeks, so be sure to work closely with the appropriate departments to pre-identify the needed recovery time objective (RTO) to help guide your plans.
5. Post-Incident Activity: Once the dust settles, conduct a root cause analysis and work to identify tactical and strategic lessons learned. Include any needed improvement to systems, hosts, policies, processes and user training. Once you understand the root cause, you will be better equipped to disrupt an attack earlier in the cyber kill chain.
6. Coordination: Certain cybersecurity incidents require reporting to CISA, but coordination with CISA and other agencies in the cyber response process can help you throughout the IR process since these agencies have the latest expertise and information to help with response and mitigation. Details of the CISA coordination response can be found in the Cybersecurity Incident Response Playbook.
If you don’t have an Incident Response Plan or are just building one, prepare to devote significant resources and participation across the company while planning, testing and implementing your plan. If you’re short on internal resources, contact us to schedule a consultation to discuss the various options for building a comprehensive IR solution.