Shields Up, Mr. Sulu!
By Chris McBeth, Senior Solutions Architect, cStor

With everything going on in the world, you can rest assured things are going to get worse. More than at any time in our history, we’re at risk of having our identity and our assets taken away in the blink of an eye. Historically, we’ve protected ourselves with physical security, but unlike previous generations, with most of our assets being virtual, we’re dealing with a new security problem requiring new “weapons” and new knowledge!
The Shields UP Initiative
The US Government’s Cybersecurity and Infrastructure Security Agency (CISA) recently announced an initiative called “Shields Up,” and it outlines steps each of us can take to fend off the evil-doers and perform our civic duty: protecting our virtual assets and those of our family, friends, co-workers and employers!
These assets are the lifeblood of this country; each of us needs to take seriously the threats we face, and take action right now! So listen up soldier, and believe me when I tell you: “Good cyber hygiene starts at home!”
From CISA “Shields Up”: “While there are no specific or credible cyber threats to the U.S. homeland at this time, Russia’s unprovoked attack on Ukraine, which has involved cyber-attacks on the Ukrainian government and critical infrastructure organizations, may impact organizations both within and beyond the region, particularly in the wake of costs imposed by the United States and our Allies. Every organization large and small must be prepared to respond to disruptive cyber activity…”
Although your office probably has things in place allowing you to securely access their stuff, the problem is in today’s mobile workforce where nearly all of us use our own devices (BYOD). BYOD includes our personal laptops, smartphones, iPads, etc. And, guess what? Securing our work assets is almost impossible if we don’t start at home with good cyber hygiene!
So, that’s what we’re here to talk about today… some quick and easy things you can do to lock down your personal accounts, taking the first step toward good cyber hygiene!
Practicing Good Cyber Hygiene
What I’m specifically talking about is 2-Factor, or Multi-Factor Authentication (MFA). Basically, it’s a way to lock down your accounts so no one else can get in, snoop around, hijack your identity, steal your cash, or start sending your friends and coworkers pathetic pleas for money!
In a nutshell, it’s the single most effective (and easy!) thing you can do to secure your cyber world. It creates at least two steps to verify it’s really you, before allowing anyone to log in or make changes to your accounts… changes like password resets, money transfers, changes to your address of record and more!
Microsoft says MFA is “99.9% effective” at stopping attacks, and I believe them. I recently conducted an informal survey online, and the results were shocking but not surprising. Meaning, I was shocked at how many people claim they know what they’re doing, but not surprised to learn few of them really practice what they preach!
Here’s the survey if you want to take it! https://www.surveymonkey.com/r/MQ2K3HY
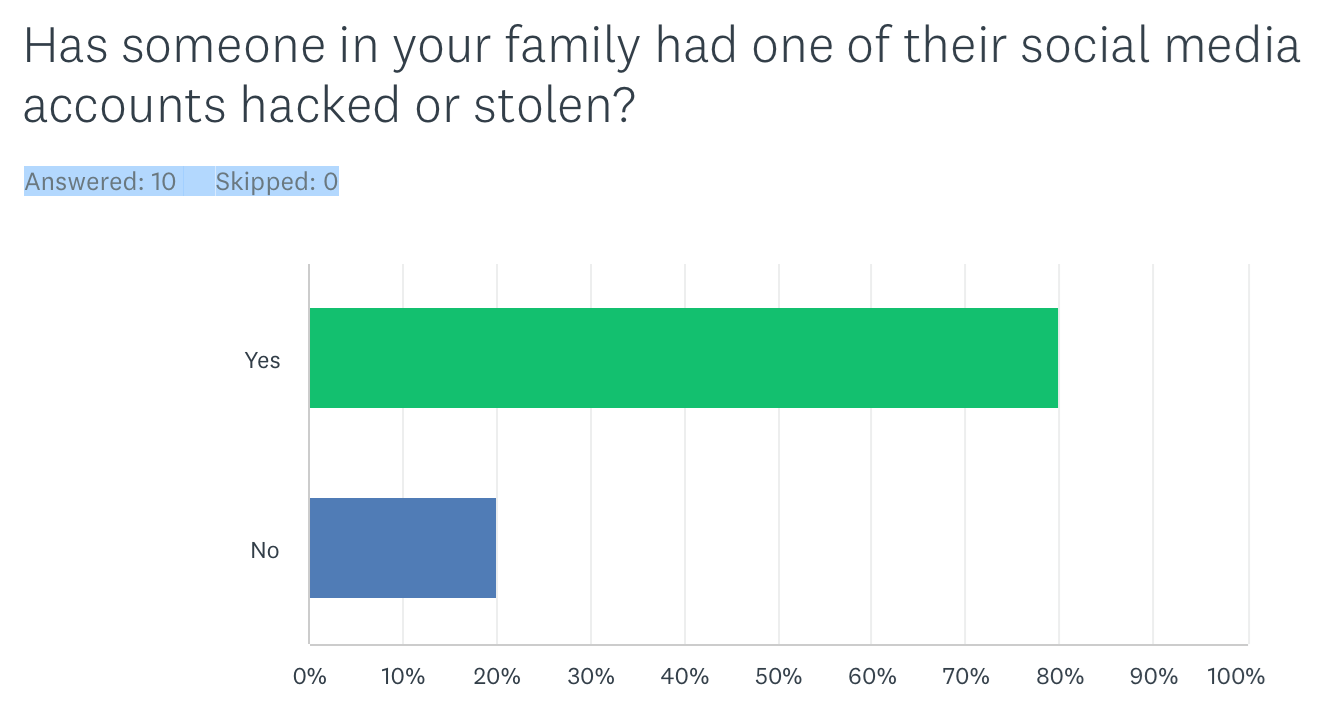 One question was particularly alarming: 80% of respondents said yes!
One question was particularly alarming: 80% of respondents said yes!
Whether we’re talking about work or home, it doesn’t matter. Thieves are everywhere and they don’t discriminate. They’re happy to steal your personal identity, your social media accounts, and just as happy to break into your work email and start wreaking havoc.
So, the first and most critical thing to lock down with MFA is email. Start there and prioritize the rest. Whether you’re young or grown up with children, you’ll want to take care of yourself first, then move on to helping others. Just like on an airplane, “put your mask on first, then assist others;” it doesn’t do any good to help someone put on the oxygen if you pass out in the process, killing you both!
That’s a bit of an extreme analogy, but now that I have your attention, read on and I’ll give you some easy, practical things you can do to secure your own cyber assets. Then, if you’re really smart and have the time, you can leverage your newfound knowledge and move on to help your family, friends and co-workers!
Securing email is not too hard. If you use Gmail, Hotmail, Office 365, Outlook, or even your internet provider’s free mail client, you can easily activate two-factor authentication using their account settings. If you’re on your phone, look for the little gear icon or the three dots “…” in the corner. Those are usually the shortcuts to account settings that allow you to enable MFA.
Each of the accounts you secure with MFA will give you a choice between SMS (texting), using a Code Generator (like Google Authenticator), or other options like printing a “recovery code” in case someone hijacks your account and you can’t get in. The important thing to remember is 2-Factor (2FA) or Multi-Factor (MFA) accomplish the same thing, and since the process to enable these are different for all your accounts, there isn’t an “easy button.” It’s going to take a little bit of time and patience. In the end, it pays off with huge dividends because you can avoid all the lost time and frustration of trying to recover these accounts once they’re hacked.
Another great thing about doing this for yourself is that we all have family, friends, or kids – and if you’re like me and my wife, parents – who are “tragically underequipped” to protect themselves against cybercriminals. Learning to do this for ourselves is sort of a new-age responsibility that prior generations would have never thought of, and it’s a critical time to teach ourselves and everyone around us to start taking personal cybersecurity very, very, seriously.
This conversation is really important to have with everyone, and it’s important to keep having the conversation to make sure they know it’s serious, ongoing, and never-ending… so let’s get started going over the practical ways you can get it done.
Key Steps to Enabling MFA
Here’s a really basic outline of what you’ll want to do:
- Start with email
- Activate MFA on that account
- Immediately change the password
- Log out all devices using the old password
- Log back in using your new password -and- your new code sent via text or generated with a code-generator like Google Authenticator
- Now, go to each of your online accounts and do the same thing one after the other, and don’t stop until you’re done!
Like I said before, I think it makes perfect sense to start with email and work your way through a list after that. Prioritize based on the level of vulnerability, importance to you and so on. If you have a lot of money in your 401K or in your bank, that would probably be a great choice to lock down with MFA. The next logical choice would be social media, specifically Facebook and Instagram. They are notoriously easy to hack into using leaked passwords sold on the Dark Web. Don’t ask how they get them… it’s scary if you dwell on that. The important thing to focus on is that it’s easy to activate MFA, change your passwords, log out all devices, and re-login. When you do that, it locks out anyone who may have hacked your accounts and makes it much harder for them to get back in.
I will make this offer: if anyone reading this wants more information on how to do this at home or at work, don’t hesitate to reach out. My work email address is chris.mcbeth@cstor.com. As a Certified Cybersecurity expert in Privileged Access Management (PAM), Identity and Access Management (IAM), and Multi-Factor Authentication (among other things!), I would be happy to share the lessons learned having done this for a lot of customers over the years… both big and small. In the meantime, look below for some useful links to activate MFA on your accounts. To find others just search the applicable application name plus the words “2-factor,” then hit search. Look for the official FAQ that’ll have the name of the product in the URL like https://help.instagram.com/566810106808145. That’s how you know it’s legit, by only going to the associated company’s actual FAQ.
In addition, here’s another trick I’ll teach you. I’ve embedded some helpful links into the words below so that there isn’t a giant list of characters. The problem is, that link could take you anywhere. What’s the trick? If you hover your mouse pointer over the hotlink, it’ll give you a preview of where it’s going! You always want to make sure it’s a legitimate site by confirming it will take you to Google, Microsoft, Facebook, Instagram, and so on. Now you know!
If you’ve read this far, I’m sure you’ve reached the limits of your patience. So, I’ll leave you with one last nugget. The first step to recovery is admitting you have a problem. So, admit it, “Google” it, and embrace the fact that MFA is an absolutely critical step you need to take today. Don’t wait, SHIELDS UP!








